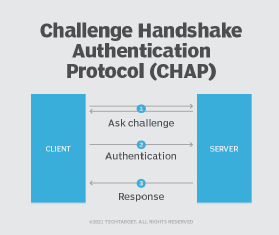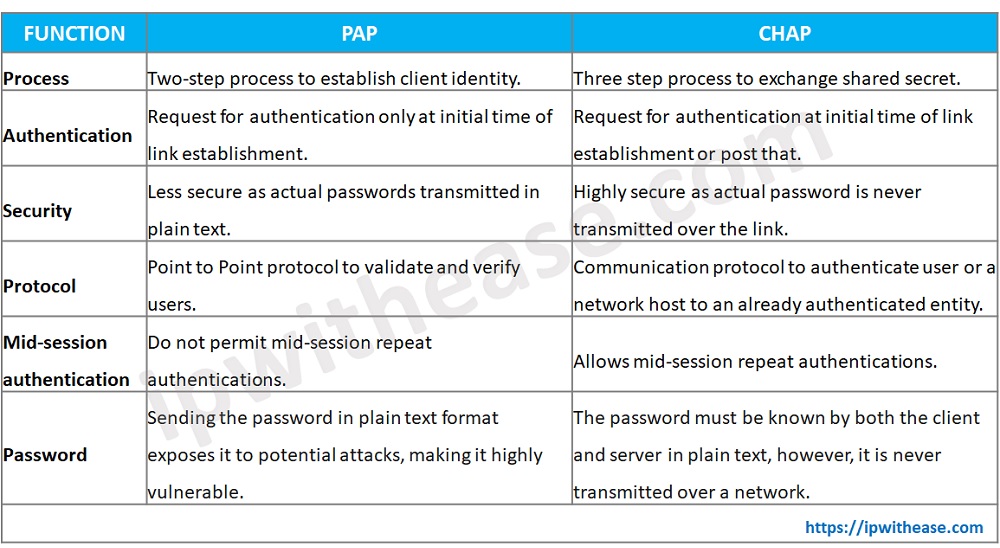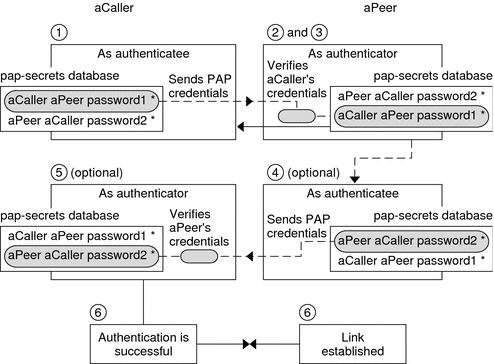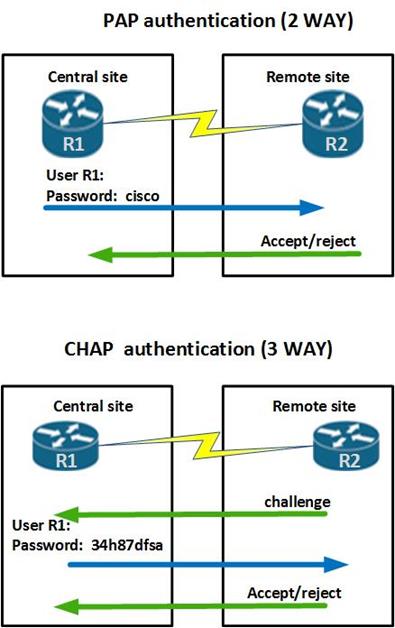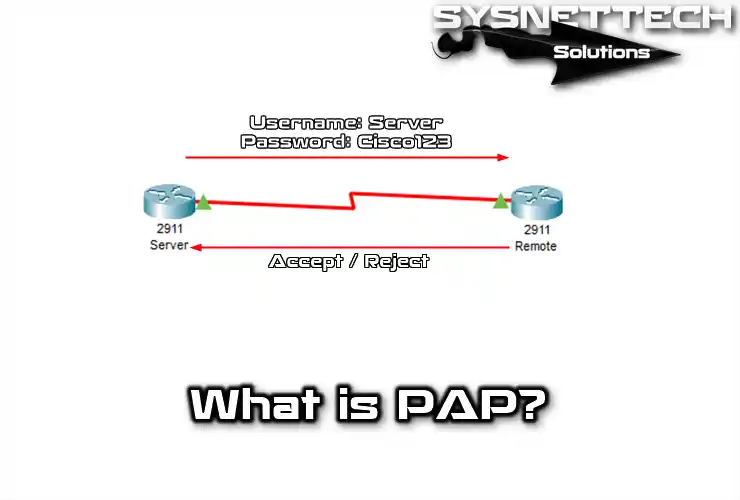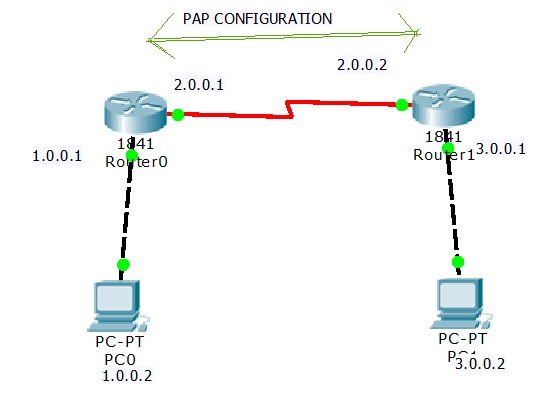
PAP(Password Authentical Protocol) Configuration on cisco router – Learn Linux CCNA CCNP CEH CISSP CISA Penetration-Testing Bug Bounty IPv6 Cyber-Security Network-Security Online

Pap Password Authentication Protocol Acronym Stock Illustration - Download Image Now - Acronym, Business, Computer - iStock
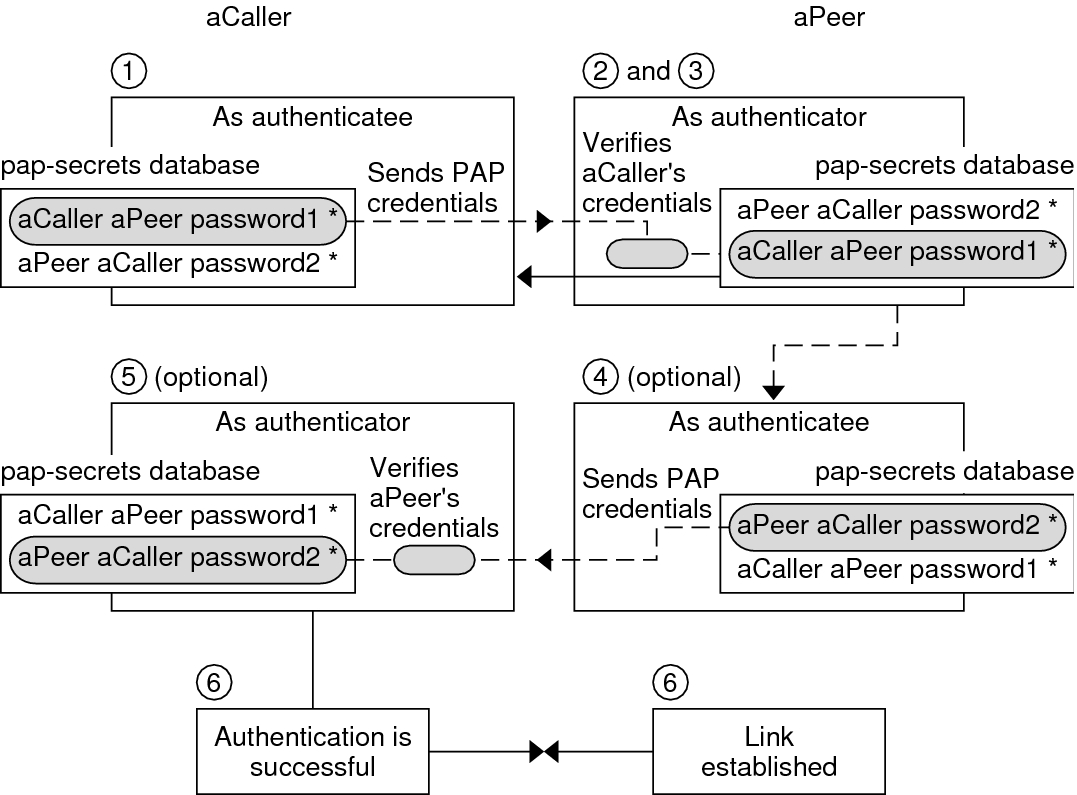
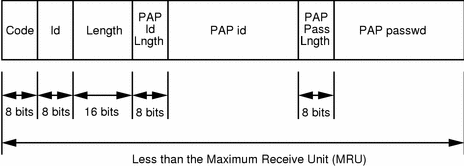
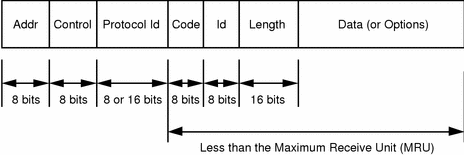
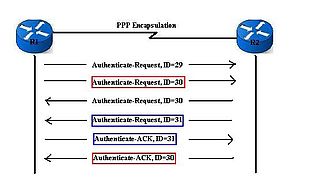
Password Authentication Protocol (PAP) - Managing Serial Networks Using UUCP and PPP in Oracle® Solaris 11.2
GitHub - Lithium876/PAP-POC: A proof of concept of how PAP (Password Authentication Protocol) works when authenticating users. This POC focuses on the fact that this protocol sends passwords our the network in